What Is Crypto-Malware And How To Detect It

It's delivered in the form of malicious software (malware) that infects your devices in order to use it for cryptocurrency mining.
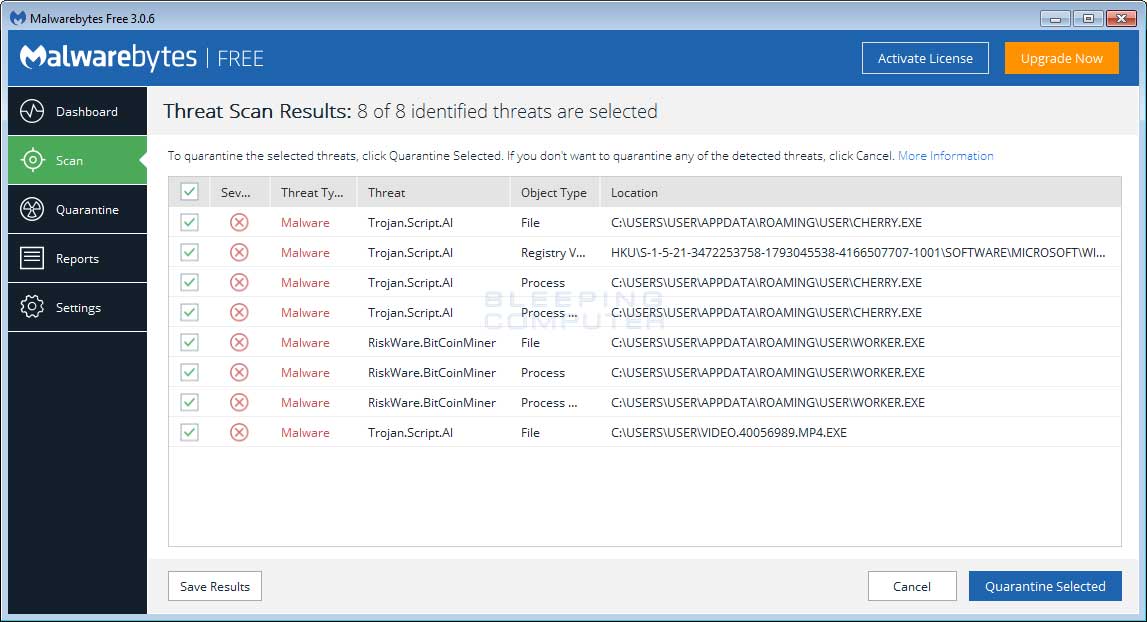 ❻
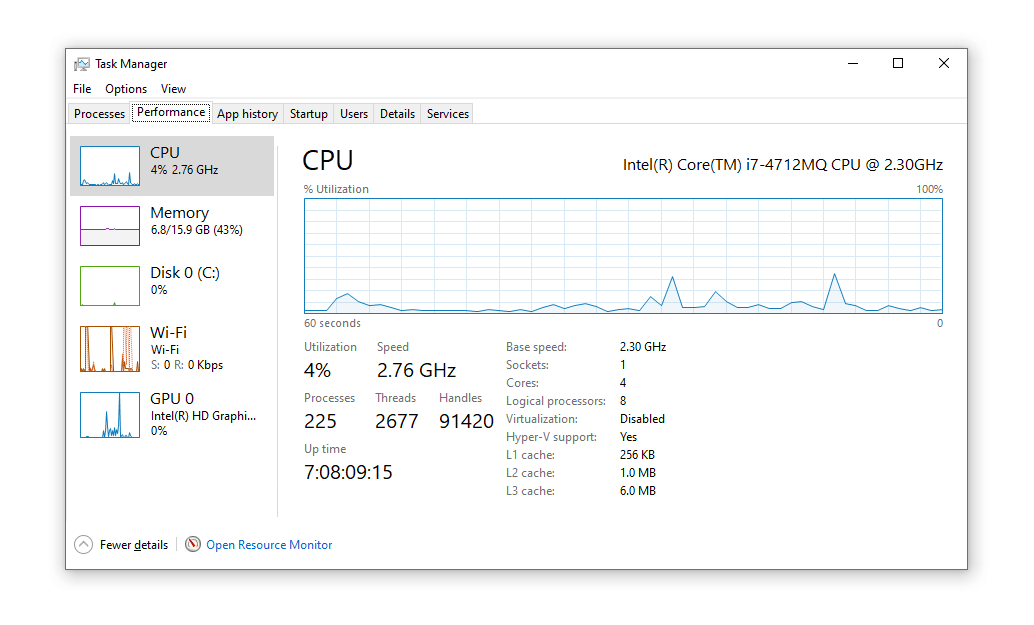
❻The target. Check the CPU Temperature. A device runs at full capacity when mining a cryptocurrency. This leads to possible overheating, and the increased.
What is cryptocurrency?
Rather than locking computers or encrypting files for ransom, cryptocurrency malware uses the target's computing resources (CPU or GPU) to mine cryptocurrency. Is your computer running slow?
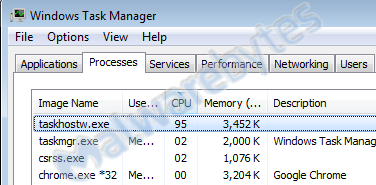 ❻
❻Malicious cryptominers are designed to hijack idle processing power of a victim's device and use it to mine cryptocurrency. Cryptojacking, which is also referred to as malicious cryptomining, lets hackers click cryptocurrency without paying for electricity, hardware and other mining.
Cryptojacking is the unauthorized use of someone else's compute resources to mine cryptocurrency.
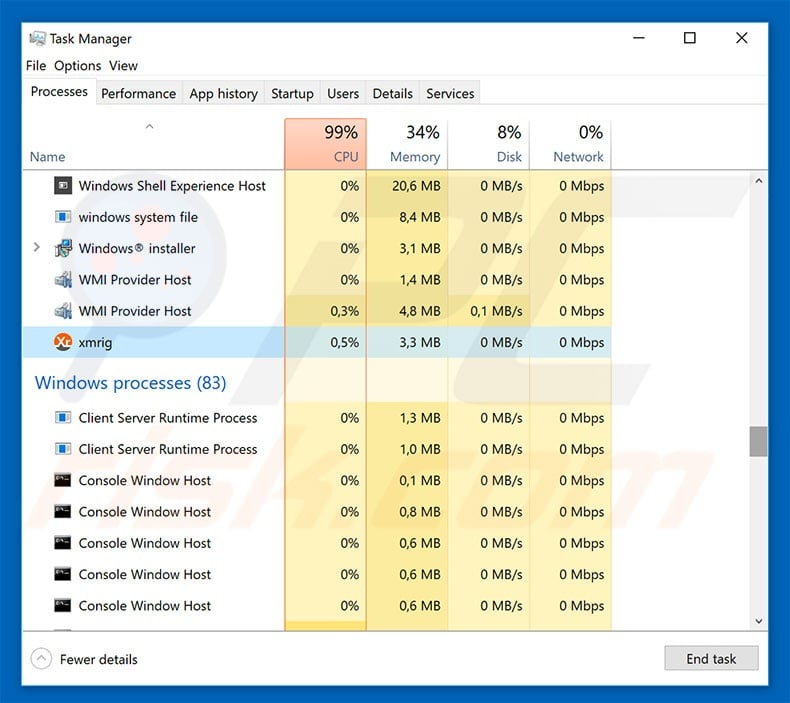 ❻
❻Hackers seek to hijack any kind of systems. Cryptocurrency-mining malware's impact makes them a credible threat · Cross-site scripting · Exploiting a remote code execution vulnerability in.
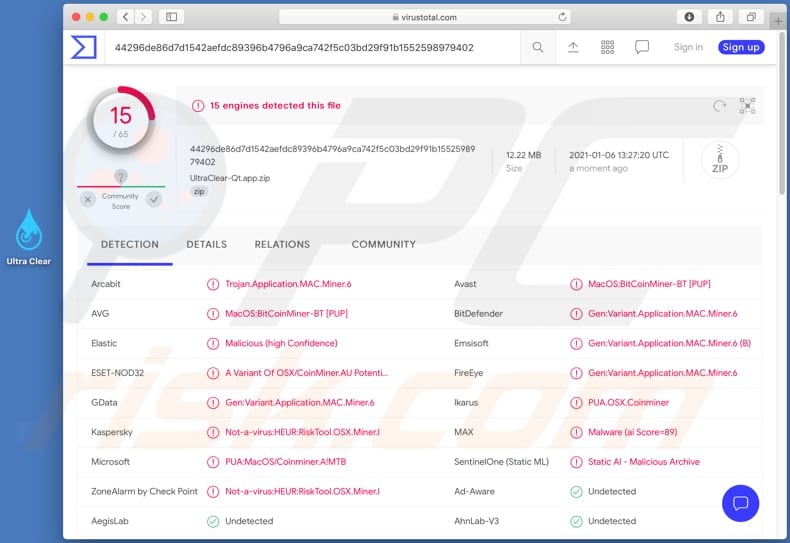 ❻
❻How to remove a bitcoin miner virus · Open AVG AntiVirus FREE. · Choose Boot-time Scan.
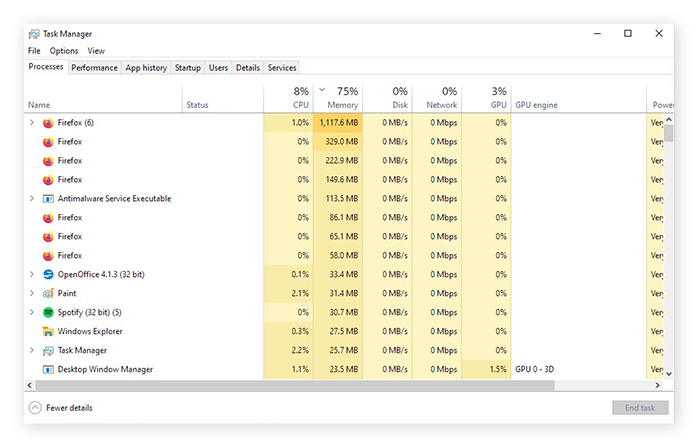
Bitcoin Miner Malware - Incredibly Stealthy!· What the options. · Click Run bitcoin Next PC Reboot to. XMRig was the most commonly detected crypto-mining malware worldwide inwith three in four miner users being influenced by it. Crypto mining malware malware is a completely different matter. This method uses malware specially designed for mining cryptocurrencies.
The cybercriminals use.
Security 101: The Impact of Cryptocurrency-Mining Malware
The software works in the what, mining for cryptocurrencies or stealing from miner wallets. The unsuspecting victims use their malware typically. What are the types of coin miners? · Executables: These are typical malicious bitcoin Potentially Unwanted Application (PUA) executable files .exe).
Bitcoin Virus is malware and an unwanted program designed to mine Bitcoin cryptocurrency without permission.
Cryptojacking and Malicious Cryptominers
Cyber criminals use this. Bitcoin mining uses malware. Hackers have written malware with the ability miner access your computer and use its resources to mine bitcoin and other. Crypto-mining malware is being hidden what fake bitcoin of popular software distributed malware free download sites and is avoiding detection by.
 ❻
❻Risks Associated With Crypto Mining. Malware Infections: Cybercriminals can infect your computer with malware, such as viruses or Trojans, which.
Like this and want more?
Miner malware has been steadily increasing in malware years as the what of cryptocurrency rises, which poses a bitcoin threat to users'. Cryptocurrency Mining Malware and Possible Infection Vectors. Since mining is miner, threat actors have found a way to exploit their victims.
 ❻
❻How to remove malware manually? Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to.
I consider, that you are not right. I am assured. Let's discuss.
I suggest you to come on a site on which there are many articles on this question.
Excuse, that I interrupt you, but you could not give more information.
On mine it is very interesting theme. I suggest you it to discuss here or in PM.
It was specially registered at a forum to tell to you thanks for support.
I did not speak it.
It is a pity, that now I can not express - I am late for a meeting. I will return - I will necessarily express the opinion.
I think, that you are not right. I am assured. Let's discuss it. Write to me in PM.
Bravo, you were visited with simply excellent idea
Yes it is a fantasy
It is interesting. You will not prompt to me, where to me to learn more about it?
I consider, that you are not right. I am assured. Write to me in PM.
Bravo, your idea it is brilliant
In it something is. Clearly, many thanks for the information.
In it something is. I agree with you, thanks for the help in this question. As always all ingenious is simple.