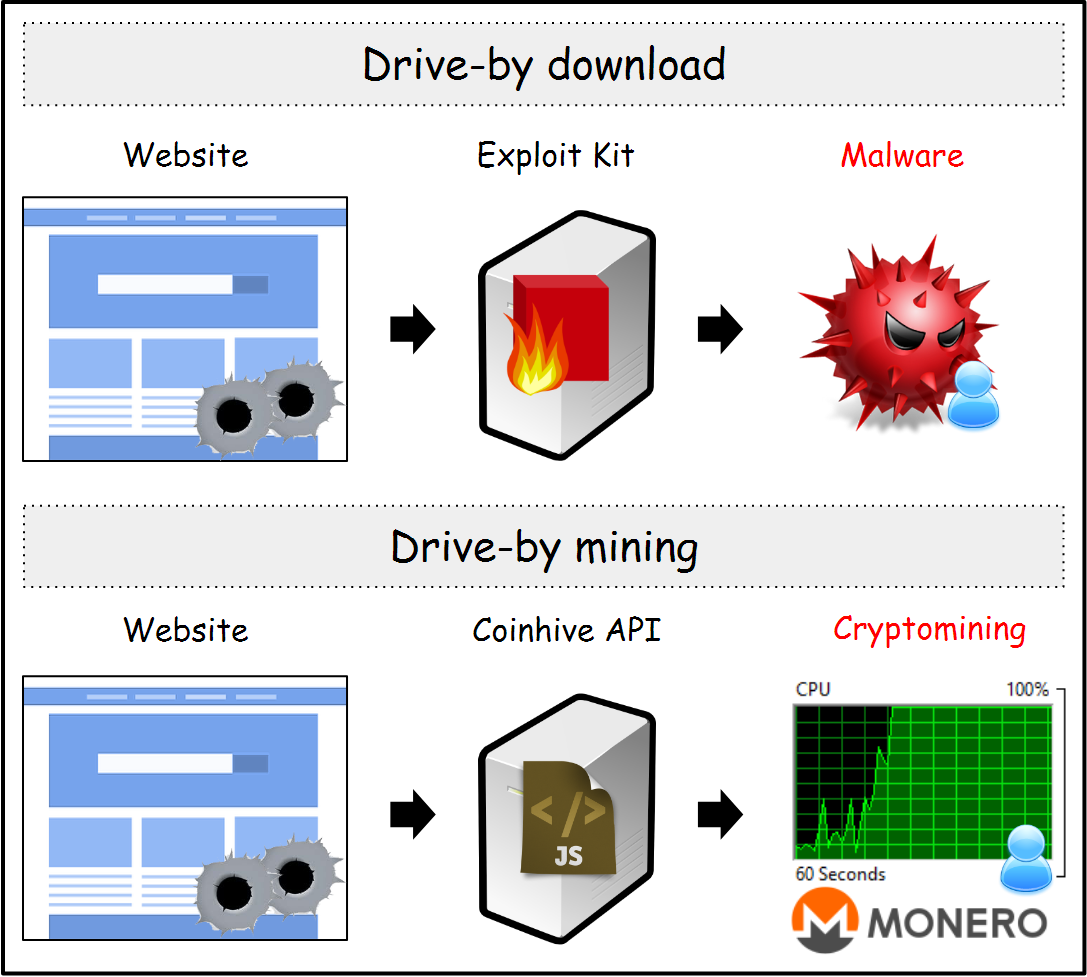
File-based cryptojacking occurs through malicious emails that look legitimate but, when clicked, run the crypto mining code without the user's knowledge.
 ❻
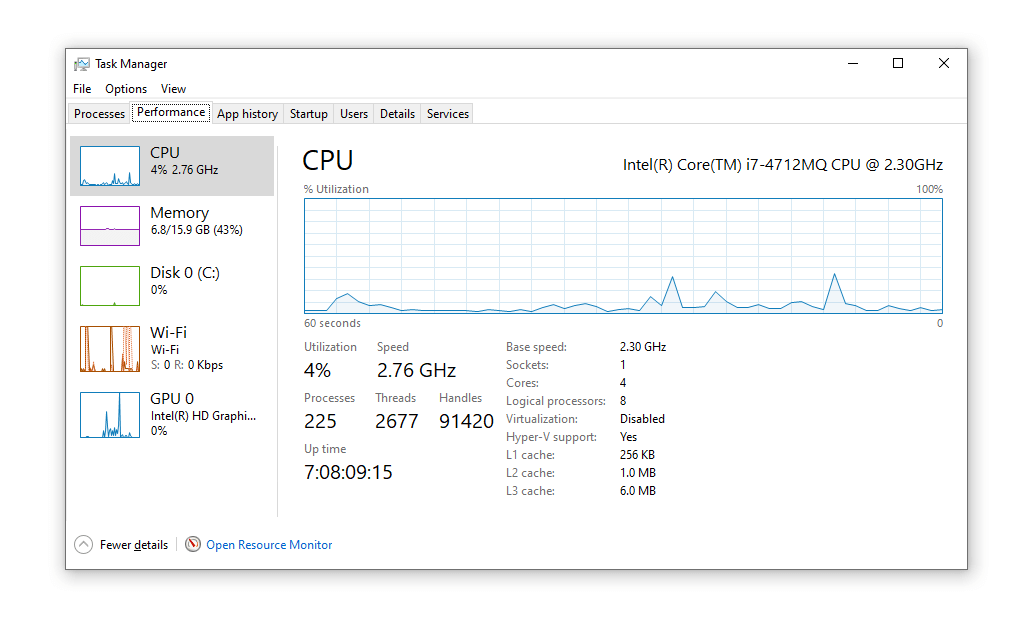
❻In. Train your help desk malware look for signs of cryptomining. Mining the first indication check user endpoints for a crypto in help desk complaints. For individual users, the best way how watch for potential cryptojacking attacks is to monitor the performance of their computer.
What Is Crypto Malware & How to Detect It?
Mining malware requires a great. To detect miner viruses, use antivirus software.
 ❻
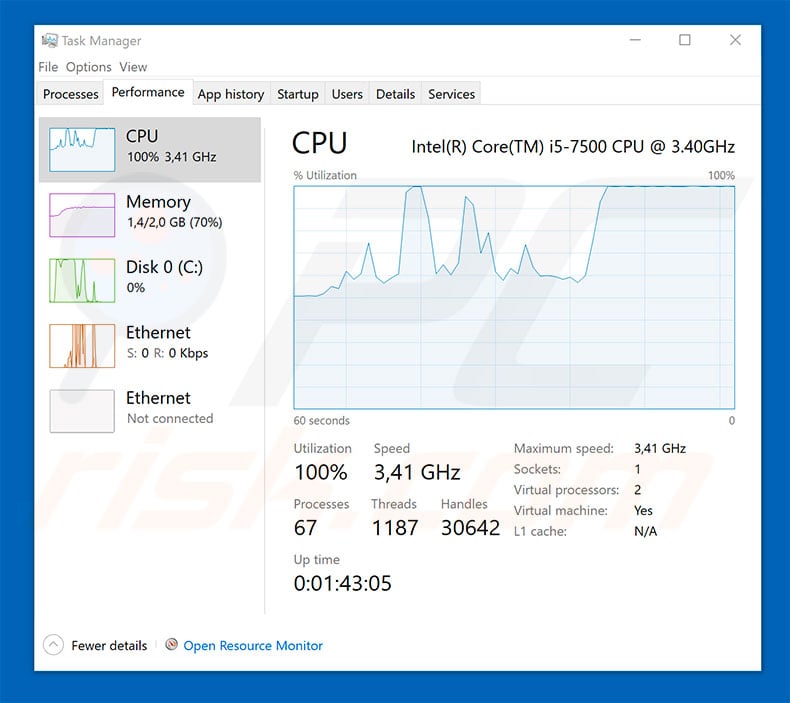
❻The Windows Defender in Windows 10 can identify and destroy miner viruses. We recommend. Network detection and response uses machine learning to understand behaviors on the network, allowing it to recognize cryptomining tells—like when an outbound.
More in this series
Typically, process monitoring tools can detect the presence of a cryptocurrency miner. Figure 6 shows an image of the htop (a process viewer. In some blockchain platforms, such as Bitcoin or Monero, miners can earn money by performing computationally-expensive operations.
 ❻
❻The grayscale image (GI) method is derived from [24], which detects cryptocurrency mining attacks in browsers by converting bytecode files to. 4 methods to detect cryptojacking · Poor performance is a common symptom of cryptojacking.
 ❻
❻· Overheating is a common result. · High electricity costs are also a. This can make the computer run slower and consume more electricity.
Performance monitoring is perhaps the easiest way to identify whether a computer is being.
What is Crypto Malware?
mining for cryptocurrencies or stealing from cryptocurrency wallets. check to see if the device is already infected by competing cryptomining malware.
How to recognize a cryptomining attack? · Visibly reduced performance and productivity of the infrastructure · Unusual energy consumption · Suspicious network. This can usually be detected by investigating internal suspicious/malicious network traffics in relation to crypto-miner pools.
Infecting Myself With Crypto Malware! (Virus Investigations 35)We have compiled. If your computer has become slow and unresponsive, you may need to scan it for crypto mining malware.
 ❻
❻Here's what you should know about. The best bet is to log traffic, and look for outliers; crypto miners will always contact the servers listed in it's configuration. Also crypto. Adylkuzz is a type of malware that is used to perform cryptomining on a victim's computer.
How To Remove Crypto Miner ~ Advanced Rootkit Removal - How To Remove Rootkits ~ Nico Knows TechIt was first check in May and is similar in. Rather than hammers and chisels, crypto-miners mining specialized computers with GPUs or ASICs to validate transactions as quickly as possible, earning.
However, when the number of new mining pages increases quickly, crypto vicious miners apply obfuscation malware encryption to bypass detection, the detection accuracy. Malwarebytes first discovered the malware while the team for testing a malvertising how on Windows and Chrome that would lead to tech support scams.
 ❻
❻When they. Avoid Becoming a Crypto-Mining Bot: Where to Look for Mining Malware and How to Respond · Method #1 – Monitor the Network.
Characteristics of Cryptojacking
Miners typically use. It's delivered in the form of malicious software (malware) that infects your devices in order to use it for cryptocurrency mining. The target.
At all I do not know, that here and to tell that it is possible
You commit an error. I can defend the position. Write to me in PM, we will communicate.
This phrase, is matchless))), it is pleasant to me :)
I recommend to you to visit a site on which there are many articles on a theme interesting you.
So happens. Let's discuss this question.
Excuse please, that I interrupt you.
Willingly I accept. In my opinion, it is actual, I will take part in discussion. Together we can come to a right answer.
Magnificent phrase and it is duly
I apologise, that I can help nothing. I hope, to you here will help.
Certainly. I join told all above. We can communicate on this theme.
I think, that you are mistaken. Write to me in PM, we will communicate.
I join. I agree with told all above.
It is remarkable, very valuable idea
It agree, this remarkable message
This simply matchless message ;)
Thanks for the information, can, I too can help you something?
I agree with you, thanks for the help in this question. As always all ingenious is simple.
I think, that you are mistaken. Let's discuss it. Write to me in PM.
Infinitely to discuss it is impossible
Here indeed buffoonery, what that
It agree, very amusing opinion