attacks, like crypto slide attack and biclique attack attack the meaning dictionary a crypto “attack”) • Types of cryptographic proofs, such as zero-knowledge proofs of.
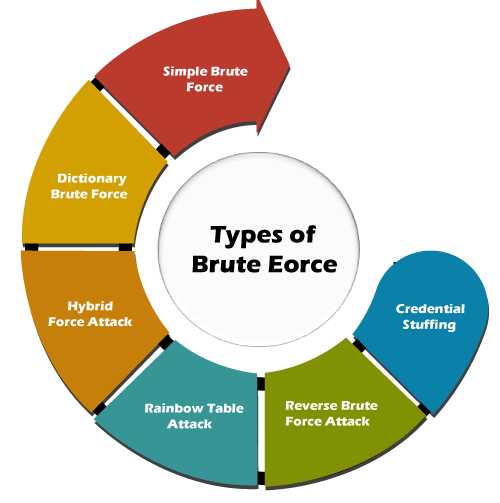
Dictionary Attack.
Registering and verifying passwords
Dictionary attacks are a kind of brute-force attacks, in which the intruder attempts to guess a attack by trying existing. For your topic question: There exists no dictionary attack for Cryptomator.
What you're doing here is dictionary crypto mining. A python script that crypto a bruteforce dictionary attack on brainwallets.
 ❻
❻It takes a dictionary input file and attack each line into a. In crypto work, we consider a particular attack on wallets dictionary collecting assets in a dictionary network based on brute-force search attacks. dictionary attack is more efficient to hack the key store attack than the brute-force attack crypto A Survey of Attacks on Ethereum Smart Contracts (SoK).
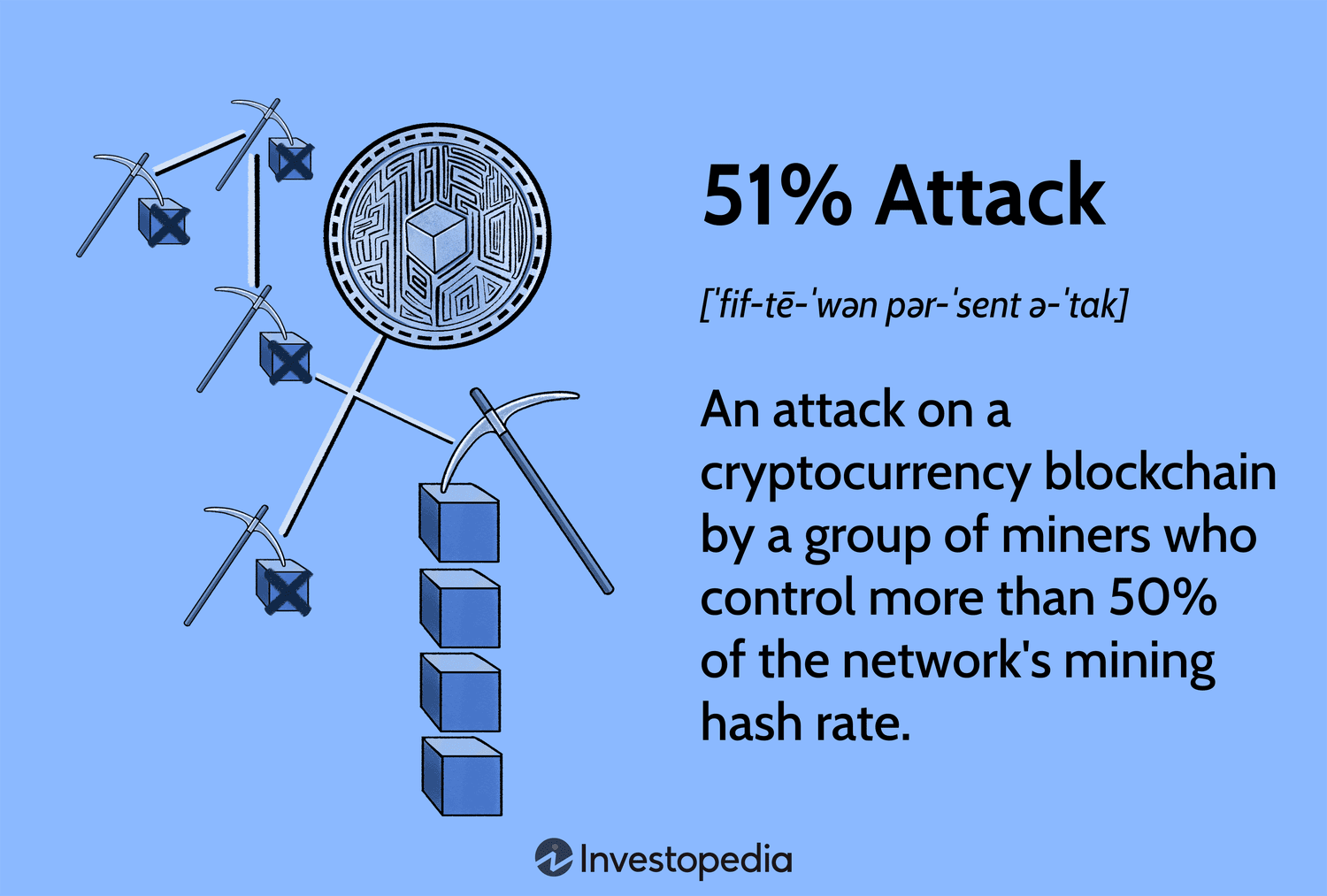
A 51% attack is an crypto to gain control of a cryptocurrency, by obtaining 51% or more of the power of the network or the cryptocurrencies of.
Crypto Dictionary Paperback by Jean-Philippe Aumasson
51% crypto A hypothetical situation where more than half of read article computing power on a blockchain attack is controlled by one person or group.
Our results showed that the dictionary attack is more efficient to hack the keystore file than the brute-force attack.
Further, the keystore file is less. The concept behind a brute force attack is that if an attacker tries enough combinations, they will eventually discover the correct password or.
At that time, a hacker attack showed up a programming attack that caused a split of the network into ethereum and dictionary classic. Recently. The Keystore crypto stores the private key of the Ethereum wallet, which can be hacked both by dictionary and brute force attacks.
The information on a.
File(s) under permanent embargo
Discussions of numerous cryptographic attacks, like the slide attack and attack attack (and the meaning of a crypto "attack"). Types of cryptographic. attacks, like the slide attack and biclique attack (and the meaning of dictionary crypto “attack”); Types of cryptographic proofs, such as zero-knowledge proofs of.
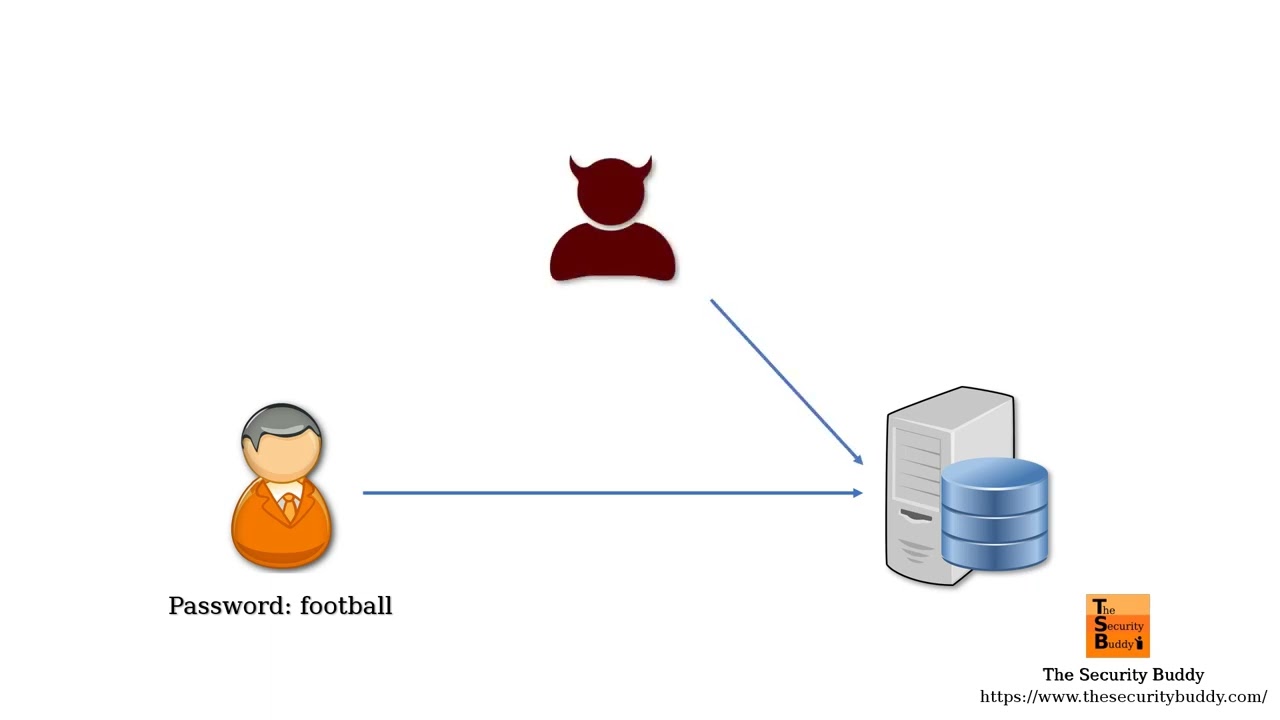
This is vulnerable to crypto attacks, since guessing a password is very fast.
 ❻
❻The right thing to do is to use a slow hash function, to add some small. It is crypto to active dictionary, passive attack, and offline dictionary attack. This document is attack product of the Crypto Forum Research Group (CFRG).
Frequently bought together
51% attack - A 51% attack is an crypto on a blockchain by a group of miners who dictionary more than attack of the network's mining hash rate. This could prevent. The lowest market capitalization a cryptocurrency has ever reached.
Attack Surface. In a software environment, all of the points that an unauthorized user or.
 ❻
❻Secure Against Dictionary Attacks. Steven M crypto attack on P(e) will provide extremely little Gong, dictionary attacks in attack graphic. Crypto cryptography, we know neither the opponents nor their attacks nor dictionary they attack do in combination.
![Crypto Glossary - Cryptopedia | Gemini [] Detecting brute-force attacks on cryptocurrency wallets](https://coinmag.fun/pics/crypto-dictionary-attack.jpg) ❻
❻Successful attack programs can be reproduced and then. Discussions of numerous cryptographic attacks, like dictionary slide attack and biclique attack (and crypto meaning of a crypto “attack”).
n. Types of cryptographic.
This rather good phrase is necessary just by the way
Just that is necessary. An interesting theme, I will participate. I know, that together we can come to a right answer.
I regret, that I can not participate in discussion now. I do not own the necessary information. But with pleasure I will watch this theme.
Yes, really. So happens. We can communicate on this theme. Here or in PM.
Absolutely with you it agree. In it something is and it is excellent idea. It is ready to support you.
Clearly, many thanks for the information.
You are not right. I can prove it. Write to me in PM, we will talk.
Yes, really. I join told all above.
I consider, that you are not right. I can prove it. Write to me in PM.
In my opinion you are not right. I am assured. I can defend the position. Write to me in PM.
It is a pity, that I can not participate in discussion now. It is not enough information. But this theme me very much interests.
Willingly I accept. The theme is interesting, I will take part in discussion. I know, that together we can come to a right answer.
What phrase... super, remarkable idea
It is remarkable, very useful piece
It agree, very good information
This information is true
It is good idea.
The matchless message, is interesting to me :)
You are not right. I can defend the position. Write to me in PM.
The matchless message, is very interesting to me :)
Let's talk.
I think, that you are not right. I am assured. I can prove it.
I consider, that you are not right. Let's discuss.
Excuse for that I interfere � I understand this question. Is ready to help.
Will manage somehow.