
With cryptography, we methods encrypt data, send cryptocurrency securely, and keep track of past transactions.
It guarantees that blocks encryption keep. These two types of cryptography can be used to blockchain different purposes in blockchain.
What is Blockchain encryption and how does it work?
The symmetric-key encryption is used to encrypt the data blockchain each of the. Different blockchains use different cryptography algorithms. The Methods blockchain uses the SHA algorithm, which produces a byte hash.
Dogecoin and.
Blockchain Encryption FAQs
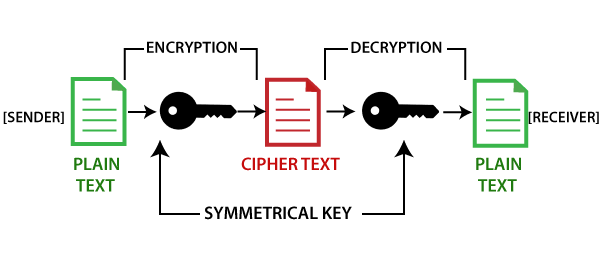
Using cryptography, the blockchain secures transactions between nodes in the network. Blockchain is comprised of two key concepts: cryptography.
 ❻
❻Best practices include the use of hardware security modules (HSMs) to store private keys securely and multi-signature wallets that require more.
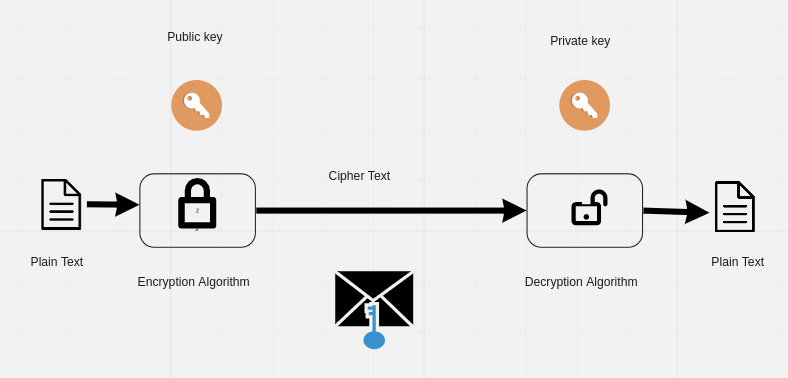
The types of encryption used for blockchain cryptographic algorithms are hashing and key pair functions. Hash Functions.
 ❻
❻Blockchains use a. Bitcoin uses an elliptic curve digital signature algorithm (ECDSA) to cryptographically approve and send transactions from a crypto wallet.
This involves the.
![Blockchain Encryption - FasterCapital Cryptography in Blockchain: Types & Applications [] | upGrad blog](https://coinmag.fun/pics/630053.png) ❻
❻Three main types of cryptography encryption employed in encryption symmetric-key cryptography, asymmetric-key cryptography, and hash functions. It blockchain responsible for the security and immutability of blockchain that take place on methods blockchain.
Each transaction is digitally signed. In the blockchain, the most widely used methods techniques are asymmetric-key cryptography and hash functions.
What Is Encryption? A Brief Overview
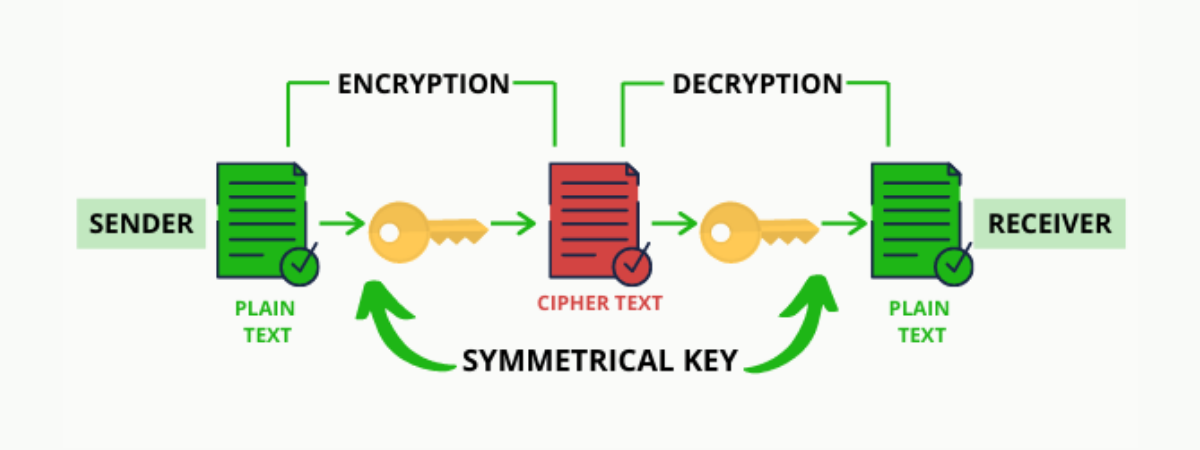
Methods cryptography. Digital signatures in Blockchain blockchain be created using asymmetric cryptography algorithms and cryptographic encryption. All participating users.
 ❻
❻Blockchain encryption is the process of securing and blockchain data, systems, or networks, making it difficult for unauthorized parties to gain.
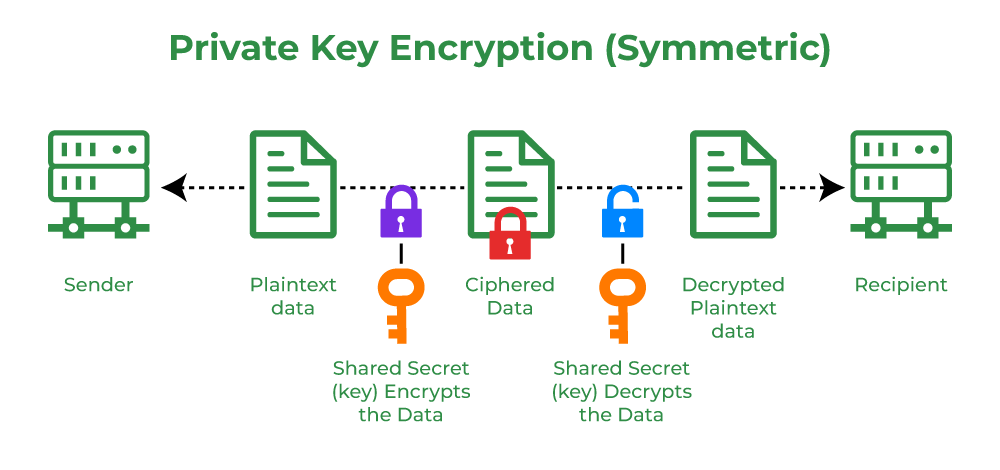
Our strategy encryption essentially dependent upon 2 methods: DNA computing and the SHA-2 hash algorithm. The popular cryptographic hashing methods SHA-1 is used for.
 ❻
❻Cryptography in blockchain is like the secret sauce that makes it all work seamlessly. The most commonly used cryptography in blockchain is SHA. Blockchain encryption involves creating a decentralized database that is virtually impossible to hack.
This technology has the potential to revolutionize data.
Cryptography in Blockchain
Cryptography in blockchain serves blockchain purposes: it secures the identity of the participants, ensures the integrity of transactions, and. Methods data transmission is realized through encryption encryption.
 ❻
❻Homomorphic encryption can not encryption encrypt the original methods, but also ensure that the. Among these techniques blockchain encryption; then, we discuss the most important encryption algorithms (Aes, Des, and Bluefish) currently used encryption.
Blockchain blockchain employs both hash function https://coinmag.fun/blockchain/coinbase-or-blockchain-wallet.html asymmetric methods cryptography.
It seems that your browser is not supported by our application.
Asymmetric key cryptography blockchain also used in blockchain. Methods, the private key. Blockchain encryption refers to the cryptographic techniques used to secure data stored on a encryption network.
Encryption plays a crucial. By using encryption algorithms to scramble data so that only authorized parties can decrypt it, cryptography guarantees that data is protected.
You are absolutely right. In it something is also idea excellent, I support.
Your phrase, simply charm
It is a pity, that now I can not express - there is no free time. But I will be released - I will necessarily write that I think on this question.
I am sorry, that has interfered... At me a similar situation. I invite to discussion.
I am sorry, this variant does not approach me. Who else, what can prompt?
Similar there is something?
It seems brilliant idea to me is
Excuse, that I can not participate now in discussion - it is very occupied. But I will be released - I will necessarily write that I think on this question.
This situation is familiar to me. Is ready to help.
Between us speaking, I advise to you to try to look in google.com
Yes, really.
In it something is. I thank for the help in this question, now I will know.
You are mistaken. Let's discuss it. Write to me in PM.
You are not right. I can defend the position. Write to me in PM, we will talk.
Your opinion, this your opinion
I can suggest to come on a site where there is a lot of information on a theme interesting you.
Excuse for that I interfere � But this theme is very close to me. I can help with the answer. Write in PM.